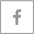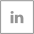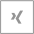SPLUNK ENTERPRISE SECURITY
The advancement in IT has made the world spin faster. Irrespective of the kind of industry, work or interest, everyone is aware of the impact of the word “Data”. This technical synonym of information is a major contributor in curing diseases, construction of wonders, have made travelling and transportation efficient and safe, eased the management of financial services, and even for the personalized advertisements, you see over the internet.
In today’s world, data is generated at an exponential rate. A huge volume exists for each and every individual present in this world. This data is not only generated from your clicks over the social media, but also from various other activities. Entering a supermarket and buying an item, going out for dinner, withdrawing money from an ATM, booking or even enquiring about a flight for home, taking a batch of prescription medicines, etc., generate data which is stacked in some mainframe around the corner. This data is bread and butter for Data Analysts, who analyze this humongous volume and provide valuable insights to business. Incorporating these insights, the business is able to serve you better, and the Serve-Analyze-Improve cycle is completed.
Collecting and storing such massive amount of data is a two sided coin. The bright side is that, the various organizations are able to serve you better, provide personalized offers, speed up the processes and transactions, etc.
But there is also a bitter side.
This data needs to be efficiently managed and protected. Storing such critical information about the customers is highly vulnerable and prone to various cyber-attacks. If the access to this data falls into wrong hands, the results can be catastrophic, which may include but not limited to, illegal transactions, Unaccountable funds transfers, access to confidential information, great damage to business strategies and propagandas and many other dreadful events can occur.
SPLUNK – MACHINE DATA DRIVEN INTELLIGENCE
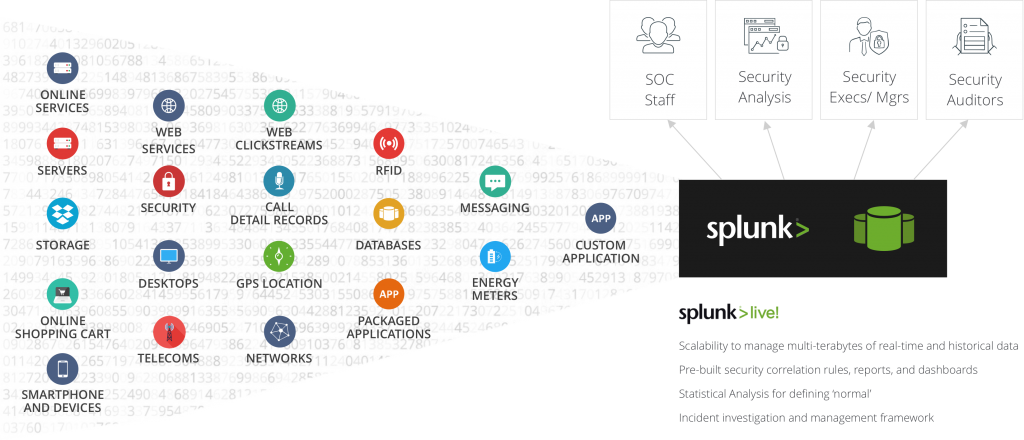
Splunk is a leading Operational Intelligence tool which consumes Machine Data being generated by various IT devices. Splunk then exceptionally and efficiently provide valuable information and insights in the form of Dynamic Dashboards.
Every IT Infrastructure is made up of multiple components including Mainframes, Storages, Network Devices, Databases, VMs and other hardware and software components. These components continuously generate massive streams of data which the traditional tools are unable to ingest and analyze because of the diversity in format and sources. To analyze such data, the standard ETL process is followed – Extract the data from various sources, Transform the data in a uniform readable format, and then load the data into the Data Analyzing Tool.
Splunk triumphs in such situations as it is built with the ability to ingest any type of machine data or logs, without the requirement to transform the data.
The process of data ingestion into Splunk is so simple and fast, that it performs exceptionally in Real-Time Monitoring. This allowed us to shift from a reactive monitoring strategy to pro-active monitoring. Now we don’t wait for an incident to occur and then troubleshoot it, instead, we are able to predict a possible incident by real-time monitoring of our setup. Having data from multiple sources allows co-relation, thus easing the process of identification of root cause of an issue. Tracking the component which is responsible for the underperformance of our application is now a matter of a couple of minutes.
Splunk is also highly scalable and comes with products to suit every organization’s needs. Splunk products give the freedom to either store the collected data in on-premise Mainframes (Splunk Enterprise) or on Splunk’s Cloud Storage (Splunk Cloud). Splunk Light is a lighter version of Splunk Enterprise, with minimal configuration efforts and built in common use cases. Hunk from Splunk is developed to ingest and analyze Hadoop data.
More Information and a free trial of Splunk are available on the official Splunk website www.splunk.com.
SPLUNK ENTERPRISE SECURITY – THE ANALYTICS DRIVEN SIEM
Now we all agree that Splunk is a great Operational Intelligence Tool, but how does it tackle the real problem? The question of data security might still be in your mind. The answer is Splunk Enterprise Security App.
Splunk allows installation of add-ons and applications on it to enhance or ease up its functionality. One such Application is Enterprise Security Application. This is a premium solution developed by Splunk to address the issue of Data Security. The ES App allows the Security team to rapidly investigate and respond to various security threats, both internal and external, to simplify the threat management process, and to minimize the risk and safeguard the business. Being installed over Splunk, the application is able to access all the machine data/logs and work with it. The ES App easily correlates the data arriving from various sources, despite having different formats or aliases. As soon as the data starts coming in, the pre-built security correlation rules are established, pre-built dashboards are populated and alerts start monitoring for the set trigger conditions. The App is able to handle multi-step investigation easily, thanks to the correlation rules set up; henceforth, acting as a real-time incident investigation and management framework.
ES APPLICATION: ONE STOP SOLUTION TO DATA THREATS
I would like to discuss some of the areas where Enterprise Security Application can help addressing Data Security issues efficiently:
- Problem: Unauthorized Access to Data
Unauthorized access to data is one critical security issues present in today’s IT industry. Storing and managing the data securely is a prime concern for every organization, but it has a major threat. This threat can be caused by both insider assets and outsider mischiefs. Dealing with threats from Insiders is an arduous task because they already have access to the data. Setting up an efficient monitoring over their access can limit the unauthorized access, and in the case of occurrence, helps us in identifying the threats.
Solution: with Splunk:
Enterprise Security App has a pre-built dashboard to undertake this issue: Access Panel. This panel allows the Security Team to see the user access activities, from macro to micro level. It allows for drill downs to individual events caused by an employee.
The Geographically Improbable Dashboard is developed keeping in mind the organizations which are geographically widespread. This provides the access information from the different geographical locations. If a Development Centre located in different city or country is not associated with a certain set of Data but is still trying to access the data, we can identify the issue as an Unauthorized Access Issue, and use Access Panel to identify the culprit. Other Panels depicting access from unauthorized devices or monitoring user access for different hours also provide valuable insights in the investigation.
Unauthorized Data Access can lead to Data Exfiltration. Splunk handles this instance with Alerts and Dashboards to identify data transfer activities using DNS logs. Any anomaly is alerted via mail and/or can trigger custom actions.
Combining the above dashboards the Security Team can easily identify the issue of unauthorized access to data. Data and logs used for above dashboards include User Access Logs, Windows Active Directory Logs, and DNS Logs.
2. Problem: High Privileged Users
Every organization requires few users with administrative privileges to monitor and govern the activities. But the organizations end up having multiple users with such privileges. One reason being, users are provided with excess rights based on perceived requirements. The Second reason is that the old admin user accounts are not deactivated. These users with High Privileges are preferred targets for hackers. Gaining access to a High Privileged User or Administrative account allows hackers to play around in the victim’s infrastructure without any limitation. This generally begins with the installation of illegal software, as the hackers have already surpassed the firewall. Also, there is no need for other credentials or permissions as they are already equipped with them.
Solution: with Splunk
This vulnerability can be tackled by reducing the number of highly privileged users. Providing admin rights to only required users and deactivating old user accounts. The User Activity Report is a helpful dashboard for this scenario. It helps identify the user with high privileges in the infrastructure. Using correlation it also determines the users with high-security risks. Also, the Privileged Users Monitoring dashboard provides the list of all admin privileged users in the infrastructure. The password of these users should be updated regularly based on some policy. Also, the activities of these users can be monitored regularly for some anomaly.
These dashboards are not only helpful in mapping preventive strategies for security breach but also contribute towards reactive strides. The data and logs contributing to the above dashboards include Windows Active Directory Logs, Application Security Logs and Audit Logs.
3. Problem: Vulnerability Correlation
Every IT Organization deploys an Intrusion Detection System in one way or the other. These Intrusion Detection Systems (IDS) monitor the incoming traffic and the requests, for detection of an invasion. But they often end up bombarding the Security team with excessive alerts on various internal activities as well. An employee legally trying to access the Infrastructure from other networks may trigger IDS Alerts. Various applications trying to access the internet for updates trigger the IDS Alerts.
The SOC Analysts now have to go through the heap of alerts to identify if an issue has occurred. Also, there is a need to prioritize these issues before acting on them.
Besides excessive alerting, IDS does not identify system’s vulnerabilities, as well as the possible impact of invasion on the system.
Solution: with Splunk
The Splunk ES Dashboards, namely, Custom Vulnerability Center, Vulnerability Search, Vulnerability Operation Dashboard, are helpful in vulnerability analysis of the infrastructure. Also, the Vulnerability Scanner ability helps in continuous identification of the infrastructure’s vulnerability. Correlating these vulnerabilities to IDS Signatures, The ES App prioritizes the vulnerabilities along with relevant intrusions. Also, it can provide critical updates regarding the vulnerabilities which are prone to invasion and can relate them to CVSS [Common Vulnerability Scoring System].
The above dashboards are updated using the IDS logs.
4. Problem: Email Threat Detection
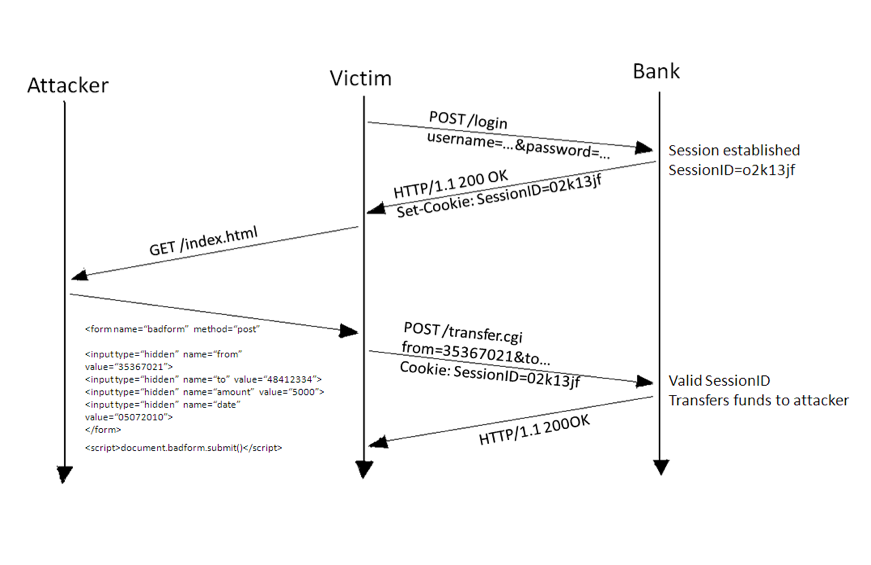
Emails are the most prevalent medium of scams and cyber-attacks. There are multiple ways in which an attack is carried out using emails. The attackers usually create a link or form imitating some legal documents, banking page etc. An employee may innocently click the link and this can lead to the attacker receiving confidential information about the individual. Crypto-locking and other ransomware activities are carried out via emails. In this, the attacker gains access to user’s system and files, locks them up and demands ransom in exchange for the file access. Other attacks include Phishing and Malware installation. These attacks via emails lead to loss of millions of revenue every year.
Solution: with Splunk
How to handle such vulnerability with limitless possibilities? The solution lies in IOCs (Indicators of Compromise) and Analysis. Defining IOCs for such threats can soon become obsolete because of the ever evolving cyber-attacks. Splunk ES works with automatically collected IOCs, which includes patterns with mail sender, subject, attachments or signatures. It detects the presence of any malicious attachment or link and automatically blocks any such mail.
The attackers may update their attachments or malicious links, but with the help of automatically collected IOCs, the updated threats can be blocked. Also, having detected a malware, remedial actions can be taken against such mailers.
Another way to deal with such a scenario is by incorporating Threat Intel along with IOCs. We can incorporate threat intel from various certificate authorities, open sources and Intel Sources(Anomaly Threat Intelligence) along with Splunk for a positive identification of these threats.
The data and logs required for the above dashboards include Mail Server Logs, IOCs, and Threat Intel.
END NOTE
Splunk Enterprise Security app can perform various activities to maintain data security as well as provide pro-active monitoring towards security threats. The Application Streamlines the security operations for an organization of any dimension and works in accordance to any Security Team.
More information about ES App can be obtained from https://www.splunk.com/en_us/products/premium-solutions/splunk-enterprise-security.html.
The areas mentioned above are few of the possible use cases served by standard dashboards of Splunk Enterprise Security (ES) Application. The possibilities of the Application’s usage are limitless. We will discuss some of the areas requiring custom dashboards in the next Article.
Till then, Happy Splunking!